ALL >> General >> View Article
Blockchain’s Contribution In Implementing Employee Safety Protocol In Workspaces!

Today, a huge chunk of employees across the globe have returned into a physical office environment and several others are scheduled to resume working-from-office after remotely working for a long time. But, the fear of getting infected with the Covid19 virus persists.
So, how could organizations maintain safety protocols at their workspaces? Well, the two most effective mechanisms that are being incorporated by enterprises to ensure employee safety are: contact tracing and maintaining digital health wallets for employees. However, there are security risks involved in both these processes and so employees may be reluctant to adopt these processes.
This post explores how Blockchain application development improves the effectiveness and enhances the safety quotient of the aforementioned processes.
Before we delve deeper, check out the unique attributes and functioning of Blockchain technology!
Blockchain ...
... Technology: Key Attributes
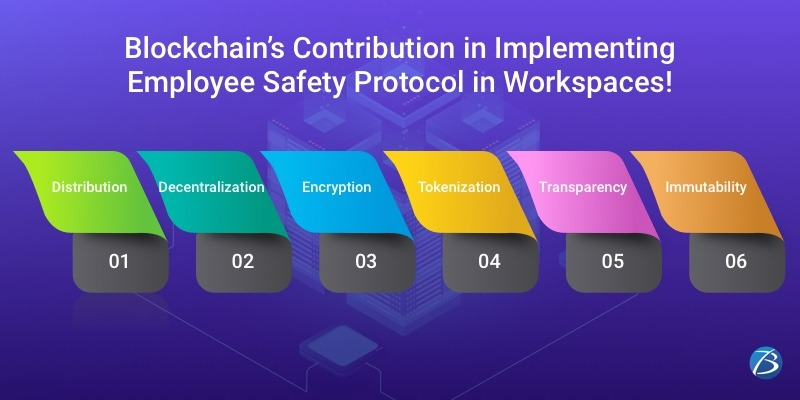
Distribution
The participants, who are a part of the blockchain, are connected through a distributed network. “Nodes” (computers) are present for operating this network. The nodes run programs for imposing the rules laid down by the business enterprise that owns the blockchain. The nodes also maintain a copy of the ledger and updates data independently, whenever a new transaction takes place.
Decentralization
Blockchain is a decentralized ledger, based on peer-to-peer technology, in which the information is distributed across the network instead of being stored by one single entity. As such, no entity can control a majority of the nodes or dictate terms. Thus, unlike the traditional approach, this approach eliminates the need for a centralized authority for controlling the network. Instead, multiple participants are authorized for managing the network – a “consensus mechanism” is employed for approving and checking transactions. Decentralization, increases reliability as the users no longer have to trust a third-party authority and also minimizes the risk of systematic failures considerably. Hence, Blockchain solutions are more transparent, secure, performant, and irreversible.
Encryption
This feature uses pseudonyms to record the participants’ details and thus ensures the security of all recorded data. The participants are entitled to control their personal details and share them only with authorized entities whenever needed.
Tokenization
With this functionality, items of value or physical or non-physical elements are converted into “tokens”. Blockchain identifies these “tokens” as “currency” within the system and these can be traded as well. Data and even a participant’s identity can be represented as the value that can be converted to tokens and then traded.
Transparency
This aspect of Blockchain imparts a layer of accountability that is a crucial prerequisite for several enterprises. All transactions can be searched for as well as traced in open Blockchain. And, to protect data privacy, granular access is provided to certain authorized users and at the same time, the data is protected from unauthorized access.
Immutability
This ground-breaking property of Blockchain rules out any third-party interference to the continuously growing chained data. Blocks are used for storing data introduced into Blockchain and these blocks are connected as well as secured by cryptography. Each block is given a unique identification number employing a cryptographic algorithm and is called the cryptographic hash function. During a transaction, blocks are time-stamped, sequentially added to the ledger, and cryptographically signed. Each block contains its own hash, transaction-related data, a timestamp, and the cryptographic hash of the previous data. As such, data once entered into the Blockchain network, cannot be tampered with.
strong>Functioning of the Blockchain Network
When somebody joins the Blockchain network, an entire copy of the Blockchain is received and the nodes verify whether every aspect is in order. This new block is then sent to all participants of the network and the block is verified by each node for ensuring that no tampering has taken place. Once successfully verified, the block is added by each node into their Blockchain and the transaction is completed.
For ensuring the authenticity of this new block, the nodes use a particular consensus mechanism. All the nodes present within the network create a consensus by agreeing on which of the blocks are valid and which of them are invalid. Any block within the network that has been tampered with will be rejected by the other nodes of the network.
So for tampering with a Blockchain system successfully, one must manipulate every block contained within the chain and then gain control over more than half of the P2P network, which is not possible by any means.
Blockchain’s Role in maintaining Safety Protocols at the Workplace
Today, contact tracing and maintaining digital health wallets for employees has become an essential prerequisite to ensure safety protocols at workplaces. And, employing Blockchain app development for architecting such solutions is necessary. Let’s explore!
Contact Tracing
What is Contact Tracing?
Contact tracing is a mechanism that is implemented for limiting the spread of communicable diseases or disease-causing viruses. This process involves the following steps:
Step 1: Identifying the infected and their contacts
Individuals infected with a communicable disease are identified and asked about their routine activities and locations visited in the recent past. This is done to identify other individuals like family members, colleagues, friends, medical practitioners/staff, etc. who were within close vicinity of the patient.
Step 2: Tracking down the contacts
Once identified, a list of all persons who have come in close contact with the patient during the past couple of days is prepared. These contacts are then tracked down and notified about the situation. They are also provided guidance on the timely measures to be adopted and the practices to follow if they develop any symptoms of the communicable disease and are advised to stay in isolation if needed.
Step 3: Follow-ups with contacts
The health symptoms of these contacts are closely monitored by conducting regular/periodic follow-ups and tests to limit the spread of the disease.
The Traditional way of Contact Tracing: Limitations
Contact tracing was implemented in the past to control the spread of various communicable diseases. Also, for tackling Covid19 the traditional approach was implemented in some countries. But, the traditional approach comes with certain limitations. The lists of identified contacts who are likely to contract the infectious disease are maintained in paper files and the contacts are notified as well as advised via phone calls or emails. So, the entire process becomes not only time-consuming but also error-prone. To sum up, the paper-based system is unorganized, incomplete, less effective owing to data redundancy, alterable, insecure, and less accurate.
Digital Contact Tracing and its Challenges
In modern times, digital contact tracing, with the use of contact tracing apps via smartphones is trending. This method guarantees prompt as well as convenient contact tracking and is being implemented for tracing down Covid19 patients and their contacts in several regions. But, this approach too, comes with its share of downsides, the key challenges being issues concerning transparency and risks to the security and privacy of personal/medical data, if the apps are not bound by strict privacy rules like GDPR.
For example, the Covid19 patients need to upload their personal data to the centralized server so that the concerned authorities can download it and use it in contract-tracing maps. But, during this process, the users’ data becomes vulnerable to risks like trajectory attacks and reconstruction of information. For this reason, many users are reluctant to share personal health information and if the participation rates are low, the apps become virtually useless.
So, the employers whose employees need to share personal data using a contact tracing application must comply with the laws mandated by the State, Federation, and Region, depending on the kind of data that is being collected. Some regions in the U.S like California have enforced privacy laws for protecting the geolocation data of individuals by providing the option of opting out or deleting obligations. But such laws do not exist in other areas of the country.
How does Blockchain-enabled contact tracing solutions resolve all challenges?
Despite its challenges, there is no other better option than using digital contact tracing app solutions for contact tracing, and integrating Blockchain technology for building such applications is the one-stop solution. Blockchain-powered contact tracing apps can successfully resolve all challenges and also enhance the efficiency, accuracy, and speed of this system. In such solutions, a symmetric key cryptographic mechanism is employed to avoid misuse of data and guarantee the privacy of users’ data. And, digital contact tracing is decentralized, thereby keeping users’ data private and secured and ruling out any chances of trajectory attacks.
Blockchain-empowered Digital Health Wallets
Why are Digital Health Wallets needed?
While the contact tracing process is needed for isolating the Covid19-affected individuals, there also needs to be an effective means of verifying that all employees entering the workplace have tested negative. For fulfilling this requirement, employees need to share their test results and immunization records digitally with third parties like the employer, TSA agents, transportation personnel, etc.
Here again, data security is essential and hence, a digital health wallet based on Blockchain is needed so that the users’ sensitive/personal data is protected from the risks of getting exposed.
How does a Blockchain-infused digital wallet function?
Persons who wish to get tested for Covi19 need to share their Blockchain-powered digital ID with their healthcare service provider. Once the test is conducted, the medical provider will upload the test results and link them to the patients’ digital credentials with cryptographic evidence, so that its authenticity could be easily verified by any third party. Thereafter, the test result is directly issued into the health wallet of patients.
On reaching the workplace, an employee is required to scan his/her QR code with a smartphone/computer application for verification. This app would then extract the information contained within the credential and check the evidence prior to displaying the test result.
Advantages of Decentralization
Blockchain entirely decouples the users’ Covid19 status from their personal information, ruling out any possibility of data reconstruction. Moreover, the data can be moved off the chain into a private database so that the owner can directly control his/her data and delete obsolete data. Thus, the decentralized platform created by Blockchain ensures the privacy of users’ data. However, for making this model work effectively, the Covid19 test results and immunization records provided by medical bodies need to be wallet-ready.
Concluding Lines:
With Blockchain-empowered systems in place, coupled up with other common safety measures like social distancing amongst colleagues, daily screening of employees, etc. employers would be able to create a safer workplace.
If you are looking for experienced and adept Blockchain app developers / Blockchain app Development Company for crafting impeccable Blockchain-powered solutions, reach out to Biz4Solutions. We are a prominent Offshore app development company in India having a proven track record of delivering outstanding Blockchain solutions.
To know more about our other core technologies, refer to links below:
Add Comment
General Articles
1. Improving Production Quality Using Ai-enhanced Sensor DataAuthor: Satya K Vivek
2. Chandeliers In Decorating Home
Author: Chaitanya kumari
3. Usa-based Cpt Coding Solutions By Allzone Management Services
Author: Allzone
4. Optical Solution Design Spain: From Concept To High-performance Systems
Author: Fotonica Gileyva
5. How Commercial Trucking In Brampton Keeps Canadian Supply Chains Moving
Author: Anuj Sharma
6. Dallas Central Appraisal District Property Tax Protest & Savings Support
Author: O'Connor & Associates
7. Create Your Website With Host Sonu Website Builder: A Step-by-step Tutorial
Author: contentcaddy
8. The Growing Demand For Ai Agent Development Services In Modern Enterprises
Author: david
9. Car Window Tinting Dubai – Beat Heat Without Fines
Author: autoglowuae
10. The Role Of A Web3 Design Agency In Bridging The Gap Between Web2 Users And Web3 Platforms
Author: michaeljohnson
11. The "smile Makeover" Checklist: What To Expect At Your Consultation
Author: 32smiles
12. O’connor - Bexar Appraisal District
Author: poc
13. Fenplast Profile: How To Choose Upvc Window & Door Profiles
Author: Fenplast Profile
14. Cosmetics Market: Trends, Growth Drivers, And The Future Of Beauty Industry
Author: komal
15. Why Automated Marketing Is Essential For Modern Educational Institutions
Author: OpenEduCat Inc








