ALL >> System-Network-Administration >> View Article
What Is Ldap And How Does It Work?

LDAP refers to lightweight directory access protocol and is a lighter version of directory access protocol. It is useful for making two steps possible at one time. There’s no need to talk to the IT department about the completion of such tasks. LDAP is a protocol and a language form that allows finding information required immediately. It works with active directory services like Active directory. LDAP makes it easy for users to find data about individuals, organizations, companies, and more by storing data in the LDAP directory. The users get authentication for accessing the directory. The LDAP authentication is required to access information which is like proving themselves who they are. The database has all the information related to users, consent information, and group which is delivered to the applications. The authentication process involves two methods:-
1. The first one is simple wherein user Id and password are recognized and the user is connected to the server.
2. The second is where the secondary service authenticates before the user connects. ...
... This is good where high-level security is required.
The developer includes a lot of coding into it to make things possible. The size limit of the search, the time taken by the server for processing the information need to be determined by the developers. The LDAP is not similar to active directories. They are the means of exchange of well-formatted messages between clients. Active directories offer a directory service that authenticates user credentials, manages domains, resources, and stores them across a network of organizations.
Working of LDAP
The employees in an office connect with LDAP an average hundred times a day. The steps involved in connecting to the server are complex. The steps in the LDAP query include session connection, query submission, finding information, and disconnection.
• The Connection to the server takes place through an LDAP port. In short, A LDAP user is connected to the LDAP port.
• The client asks or sends a request for a set of information, for example, emails, user login information, or any other organization-related data.
• The query is processed and is communicated with the directory services. The later response is delivered to the user.
• When the information is delivered and received by the client, the data is processed.
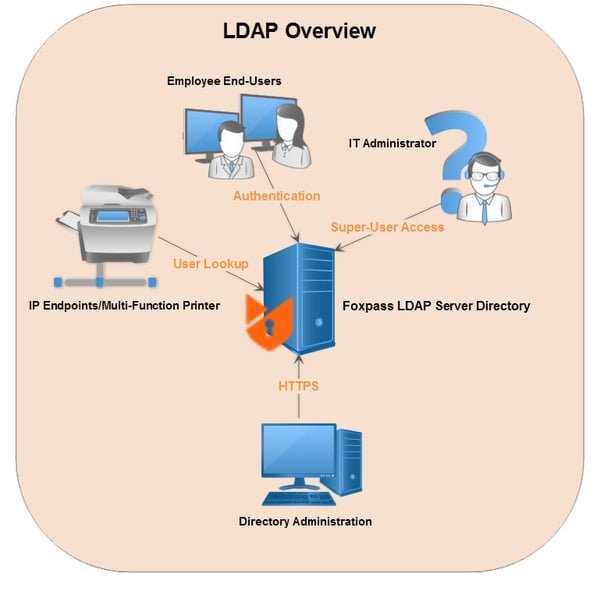
LDAP credentials are more than usernames and passwords, they help in storing telephone numbers, addresses, data about organizational structure. This has made LDAP is a strong tool in protecting organizational data across a network. They also help in connecting users with printers, files, email outlook, and other resources.
People can go through a number of operations through LDAP. They can introduce or add a new file into the database. People can delete a file from the database. Searching within the database or asking a query for getting information is possible. Comparing two files or examining them for similarities or differences and finally making changes to an already existing file are all possible with LDAP.
Concluding, every organization tends to grow with time, the need for the organization of data and arranging them into a structural manner becomes important and LDAP helps in doing so efficiently.
Foxpass brings good enterprise security practices to companies of all sizes. Our services span multiple data centers and have no single points of failure. We’re on-call 24/7 monitoring our servers. Foxpass is a well-known company in California US that are highly expert in providing good enterprise security practices to companies of all sizes. We take traditionally difficult-to-work-with protocols and make them easy to use via documentation and support for workstation, application, and server configurations.
Add Comment
System/Network Administration Articles
1. Roi Benefits Of Implementing The M-files Document Management SystemAuthor: DocSmart Solutions
2. Mems Optical Switch: High-speed, Reliable Switching For Modern Fiber Optic Networks
Author: Ryan
3. Polarization Maintaining Fiber Cable: Ensuring Polarization Stability In Advanced Optical Systems
Author: Ryan
4. Optical Fiber Alignment System: The Foundation Of High-performance Fiber Optic Solutions
Author: Ryan
5. The Real Difference Between Ai Tools And Ai Systems
Author: Orson Amiri
6. Document Manager Software: Tools To Organize Business Files
Author: DocSmart Solutions
7. Best Online Cybersecurity Training Institute In India
Author: securium Academy
8. Mechanical Optical Switch: Reliable Light Routing For Optical Networks
Author: Ryan
9. Optical Switches: Enabling Fast And Flexible Optical Networks
Author: Ryan
10. Fiber Cable Stripping Machine: Precision And Efficiency In Fiber Optic Processing
Author: Ryan
11. 20% Off Pmp® Certification: Turn This Christmas Into A Career Milestone
Author: securium Academy
12. The Fiber Jumper Production Line: Streamlining The Manufacturing Of High-quality Fiber Optic Cables
Author: Ryan
13. The Fiber Coupler Production Line: Enabling Efficient Signal Distribution In Fiber Optic Networks
Author: Ryan
14. Top 10 Cyber Threats Of 2026 And How To Prepare For Them
Author: securium Academy
15. Cloud Technology Solutions For Businesses: Improve Efficiency & Growth
Author: Venttech








